In this post:
- Trezor Safe 3 and Safe 5 wallets had security holes discovered by Ledger that could allow for remote fund theft.
- Because of the microcontroller’s susceptibility to voltage glitching assaults, hackers can alter firmware and take private keys.
- Firmware assaults are undetectable since Trezor’s authentication algorithm only checks the Secure Element and not the microcontroller.
According to a March 12 Ledger study, Trezor’s most recent hardware wallets, the Safe 3 and Safe 5, contain some significant security flaws.
According to the article, Ledger Donjon, the security research team, discovered many flaws in these devices’ microcontrollers that might provide hackers direct access to customer funds.
Even though Trezor upgraded to a two-chip design with an EAL6+ certified Secure Element, the defects still exist. According to Ledger’s analysis, all cryptographic operations are still carried out on the microcontroller, which is susceptible to voltage glitching attacks, even though the Secure Element safeguards private keys and PINs.
If abused, an attacker might acquire cryptographic keys, modify firmware, and circumvent security checks, leaving user funds at risk.
Crucial operations are not protected by Trezor’s enhanced security design
In an attempt to abandon the single-chip architecture used in previous Trezor models, Trezor released the Safe 3 in late 2023 and the Safe 5 in mid-2024. Both wallets featured an improved two-chip design.
Infineon’s Optiga Trust M Secure Element, a specialized security chip designed to store PINs and cryptographic secrets, was also included in the upgrade.
Ledger’s research indicates that this Secure Element blocks access to private information unless the right PIN is input. Additionally, it prevents resistance to hardware assaults like as voltage glitching, which were previously employed to recover seed phrases from Trezor One and Trezor T variants.
However, despite these advancements, Ledger Donjon’s research demonstrates that the microcontroller still handles the majority of cryptographic operations, including transaction signing, which is still a serious security flaw.
The TRZ32F429 microcontroller, which is actually a specially packaged STM32F429 chip, is the one utilized in the Safe 3 and Safe 5.
There are known flaws in this chip, including voltage glitching exploits that give hackers complete read/write access to the flash memory.
An attacker could control entropy creation, which is crucial to cryptographic security, once they have altered the firmware. This might result in the remote theft of private keys, which would provide hackers full access to user money.
The integrity of the microcontroller is not verified by the authentication method
Ledger Donjon discovered that although Trezor use cryptographic authentication to authenticate its devices, the firmware of the microcontroller is not checked by this method.
Trezor signs the public key, which is then embedded into a certificate when the Optiga Trust M Secure Element creates a public-private key pair during production. Trezor Suite delivers a random challenge that the device must sign with its private key when the user connects their wallet. The device is regarded as authentic if the signature is legitimate.
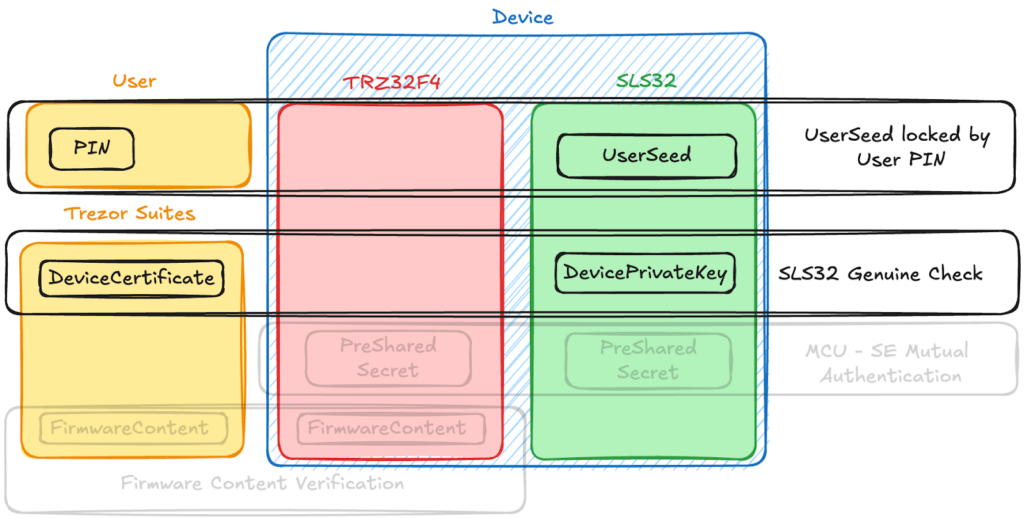
However, as demonstrated by Ledger’s study, this procedure only validates the Secure Element—not the microcontroller or its firmware.
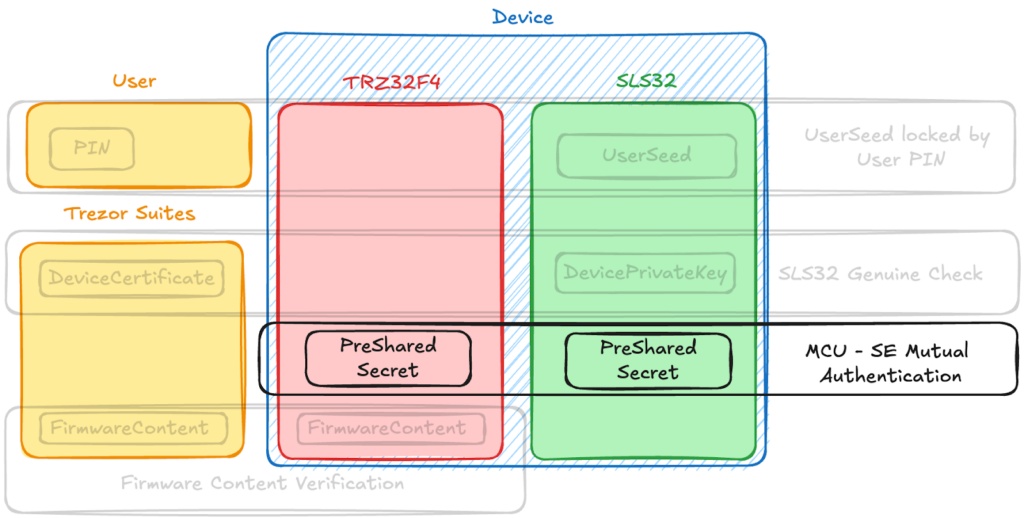
Using a pre-shared secret that is encoded into both chips during production, Trezor tried to connect the Secure Element and microcontroller. Only after the microcontroller demonstrates that it knows this secret will the Secure Element react to requests for signatures.
The issue? The flash memory of the microcontroller, where this pre-shared secret is kept, is susceptible to voltage glitching attacks.
By extracting the secret and reprogramming the chip, Ledger’s team managed to completely circumvent the authentication process. This implies that a hacker might alter the firmware and still get past Trezor’s security measures.
According to Ledger’s research, they were able to break out the pads of the TRZ32F429 onto normal headers by building a special attack board.
With this configuration, they are able to put the microcontroller onto their attack system, get the previously shared secret, and reprogramme the device covertly.
Since the cryptographic attestation scheme is unaltered, the device would still look authentic when linked to Trezor Suite after being reprogrammed.
This puts compromised Trezor Safe 3 and Safe 5 wallets in danger of being sold as authentic devices while covertly running malicious firmware that embezzles user money.
Bypassing firmware validation exposes users to
Ledger Donjon managed to go beyond Trezor’s firmware integrity check, which is a feature of Trezor Suite.
In order for the firmware check to function, a random challenge is sent to the device, which uses both the challenge and its firmware to calculate a cryptographic hash. This hash is checked against a database of authentic firmware versions by Trezor Suite.
This approach appears to be quite successful at first appearance because the device must compute the hash in real time to demonstrate that it is running authentic firmware, making it impossible for an attacker to simply hardcode a fake hash as they would not be aware of the random challenge beforehand.
Ledger Donjon, however, found a method to completely get around this defense. An attacker can alter the microcontroller’s firmware to simulate a legitimate response because it manages this computation.
The attacker can make any firmware version look genuine by altering the way the device computes the hash. Because it enables attackers to run altered software and yet pass Trezor Suite’s verification procedures, this is a significant problem.
A compromised Trezor Safe 3 or Safe 5 could therefore continue to look authentic while surreptitiously leaking private keys or changing transaction data.
According to Ledger’s study, replacing the microprocessor with a more secure one is the only method to completely safeguard the Safe 3 and Safe 5. The STM32U5, a more recent microcontroller included in the Trezor Safe 5, does not currently have any known fault injection vulnerabilities.
However, because it’s still a regular microcontroller rather than a Secure Element, there’s still a chance that new attack techniques will be found.
The vulnerabilities have already been fixed by Trezor, but the fundamental security issues still exist. Users will have to rely on Trezor’s software security measures until the microcontroller itself is completely protected, which Ledger Donjon’s research has already shown can be circumvented.
Cryptopolitan Academy: Tired of market swings? Learn how DeFi can help you build steady passive income. Register Now







